In 1984, a new Motown artist named Rockwell debuted a single featuring backing vocals by pop artist Michael Jackson. The most famous lyrics of this song (sung by Jackson) are:
I always feel that somebody’s watchin’ me…
I’ll bet Rockwell never would have guessed how spot on his song would be today. As sourcers, we are watchers. We watch for candidates and competitive intel, and many of the tools we use to monitor, profile, and reach out to our prospects placed in the wrong hands can be exceptionally creepy. We learned a lot about this from social engineer Chris Hadnagy at the most recent SourceCon conference in New York City. But I wonder how far this really goes…
Of course, people have been watching others since the dawn of time. Sometimes, it’s called stalking. Sometimes, it’s called gathering competitive intelligence. Sometimes, it’s called market research. We, of course, call it sourcing. Or social media monitoring. Whatever. It’s all watching, and it all provides you insight into your target audience. What we each choose to do with the information we gather depends on what our end goal is.
Guess what: watching, monitoring, learning, observing — this is all part of the sourcing profession. It’s just that our end goal is to help people find jobs and companies find people. For advertisers, it’s to sell you stuff. For competitive intelligence gatherers, it’s to get a leg up on the competition. So for our purposes, that removes a little bit of the ‘creep’ factor from our activities. But it doesn’t mean that the tools we use still aren’t slightly creepy. I can’t tell you how many times I’ve had prospects email me back and ask, “How did you find me?” When I revealed my process to them, some thought it was cool, and others were like, “That’s a little creepy.”
Have a look at just a couple of the weird and crazy resources that are available for public use:
Creepy
Speaking of CREEPY, Chris Hadnagy, one of our former SourceCon presenters, recently wrote a review of a product with the same name. He shared this during his presentation in February (a mere week after the product came out!), and it has since been mentioned by a couple of other reputable sites, including Lifehacker, The Huffington Post, and UK-based thinq_ and it has turned the heads of some folks. Creepy’s creator, Yiannis Kakavas, is quoted on thinq_ as saying, “…I wanted to create a tool for social engineers to help with information gathering. I believe Creepy can be of real use to security analysts performing penetration testing for the initial process of gathering information about the ‘targets’ — information that can be used later for a number of purposes.” While we sourcers are not ‘pen-testers,’ we are information-gatherers and the better we can understand the folks we’d like to approach for job opportunities the more likely we can have compelling initial conversations with them. From Lifehacker:
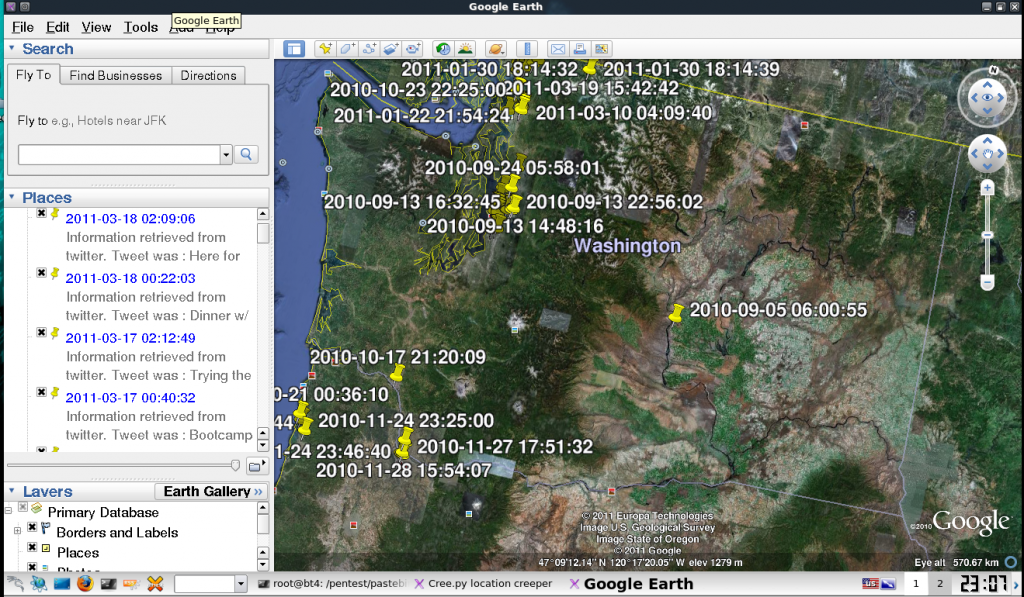
Just type in any username for a supported service [Twitter, Foursquare, or Flickr] and it will grab any and all location data it can find, from Foursquare check-ins, tweet locations, and even the EXIF data from photos posted to Flickr, Twitpic, yFrog, and other image services.
Creepy then creates a map of check-ins and photos that have been geo-tagged. One or two pinpoints on the map wouldn’t make that much of a difference, but with more check-ins and photos pinpointed, you can start to observe patterns — where an individual possibly works, where they hang out, where they live, etc. Here’s a screenshot from Hadnagy’s post of an example he ran using MY social media check-in information (I was totally aware he was doing this, by the way!):
Voyurl.com
As if Creepy wasn’t unnerving enough, you can now opt in to have your Internet activity monitored with a site called Voyurl.com. This site’s tagline is “It’s OK to look” and has ‘warnings’ on its homepage:
A little creeped out? That’s cool. But don’t worry, it’s ok to look. Besides, you can turn off voyurl at any time, for those, ahem, unmentionable sites. Plus, you can set your own filters. See, it’s not that scary.
Voyurl.com has been around since the summer of 2010 and is still operating in a private beta (though they have graciously offered invitations for SourceCon readers… email me if you want one!).
The basic idea of Voyurl is that you opt in to letting it track your web activity — it records the sites you visit and makes that information publicly available. Sounds a little creepy, yes? (Only if you’re going to site you’re not supposed to… just saying. I digress.) But once you sign up for the site, you are able to turn its tracking on and off with one click, and if you ‘accidentally’ visit a site you don’t want in your history, you can go to your own history and delete it. So while you are opting in to be monitored, you still have a great deal of control over what is being made public.
![]() The true hidden treasure of this site reveals itself when you take a look a little further into its monitoring tools. This can quickly turn into a very interesting resource from a sourcer’s perspective:
The true hidden treasure of this site reveals itself when you take a look a little further into its monitoring tools. This can quickly turn into a very interesting resource from a sourcer’s perspective:
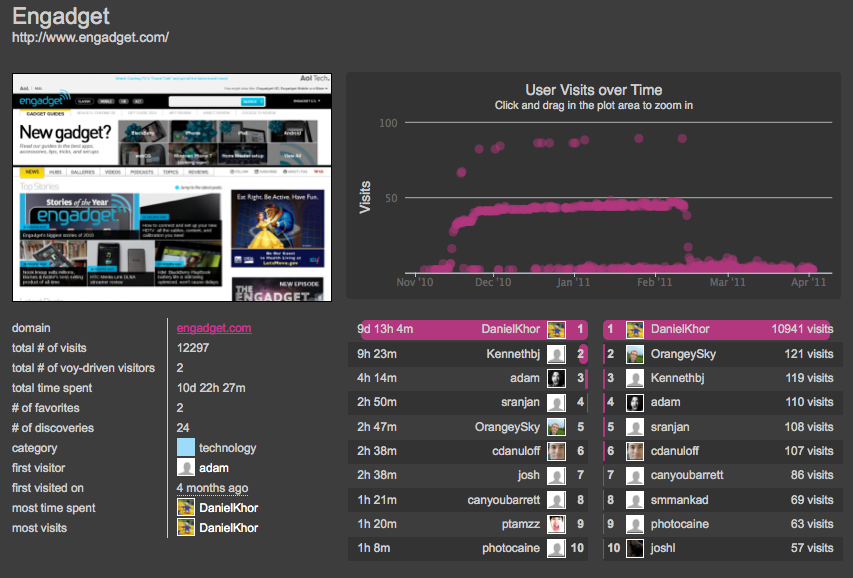
- When you click on the arrow ( > ) next to a site, it takes you to an info page on that site and shows you clicks, top user stats, visits over time (in an interactive graph — cool) and lots of other information, similar to a Quantcast type of overview, but just for Voyurl user activity. Voyurl’s creator, Adam Leibsohn, told me that the collected data represents data for all participants who have accessed that URL or domain with the plugin active.
- You can manually enter tags for sites and comments on your and others’ browsing history using the Comment button. From a sourcing standpoint, you can ‘surf’ your company’s job openings or company information and leave tags and comments for people to easily find your openings.
- You can very easily share a site you’ve just visited via Twitter or Facebook using the Share button.
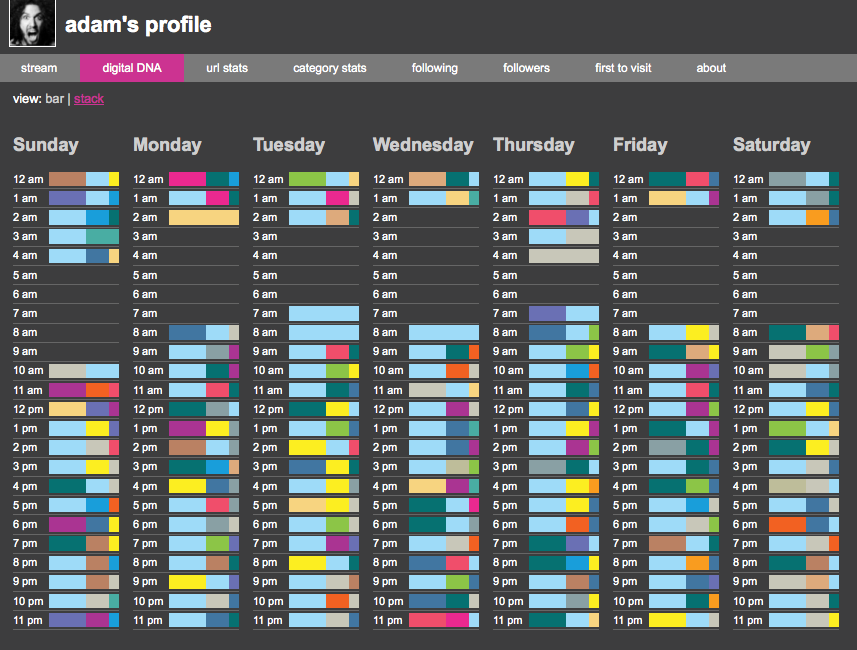
- Clicking on a Voyurl user brings you a wealth of information about their web activity. For example, by clicking on ‘Digital DNA,’ you can take a look at what time of the day that user is surfing the Web and what categories of websites they are hitting. Check out the screen shot below from Leibsohn’s web activity. Other information you can check out for individual users includes their entire browsing history, on what sites they spend the most time, whom they follow and who follows them, and of course a profile (which must be entered manually even though you can connect several different social media accounts to Voyurl when you register).
Leibsohn is a friendly guy and obliged me by answering a couple of questions I had about the site:
Q: When you leave a comment or assign a tag on a visited website, does that user receive a notification that such an activity has been done?
A: Yes. Comments, favorite-ing, and tagging all trigger emails to the user who was the genesis for the URL.
Q: how are the tags assigned that show up attached already to a site when you click on Comments?
A: It’s a blend of user-based categorization and merging data from various third-party sources.
Q: Will you eventually be able to sort searches based on the geographic location of the user?
A: Yes.
Q: When filtering ‘Tops’ (icon at the top with three bars), can you apply this filter to just those whom you follow? Or is this only applicable to all users?
A: Right now, it’s only applicable to all users, but we’ll allow you to segment out and trend just your own friends (i.e. those whom you follow) shortly.
There are, of course, some bugs that need to get worked out. Often when you try to get site stats, an error message comes up that site traffic is too heavy to accommodate your request. Also, as a sourcer I would love to see the search support full Boolean as well as search not only the URL and comments/notes but the full text of the website itself. Liebsohn has said they are “currently thinking about ways to try to expand the search functionality to make it dig deeper both effectively and safely.”
In a recent Time.com article entitled Data Mining: How Companies Now Know Everything About You, author Joel Stein says, “You know how everything has seemed free for the past few years? It wasn’t. It’s just that no one told you that instead of using money, you were paying with your personal information.” (emphasis added) The information that these two tools monitors is elected to be shared by the users — no one forced them (or you!) to opt-in to being monitored or to share locations and activities with the world. Payment for services doesn’t always come in the form of monetary exchange. Sometimes it comes in the form of having your life activities watched.
It used to be that watching others was a one-sided activity. But today, it’s become much more of a two-way ‘relationship.’ That is, we invite people to watch us. Yes, that’s right…we are exhibitionists — and we are also voyeurs. Don’t think so? Test yourself — do you:
- Have a Facebook account? Comment on others’ walls?
- Have a Twitter account? Send @ and DM messages to others?
- Have a Foursquare or Gowalla account? (okay, that’s a pretty obvious one)
- Surf the internet with a free web browser?
- Have a free email account?
- Buy stuff online?
- Take advantage of free product/service offers that request contact/personal information?
GOTCHA. You’re watching, and being watched. And you’re opting in to being watched. Virgin Mobile’s new set of commercials provides a humorous look at the capabilities of our mobile monitoring activities.
In the wrong hands, tools like Creepy and Voyurl.com can be used to harm individuals. In the right hands, wonderfully personalized outreach can be achieved to give individuals what they want and need in life. Use discretion when sharing information because you never know who is watching. And as sourcers, take care with the information you discover about others — use your sourcing superpowers to bring awesome opportunities to people. They’ll appreciate it more than you could ever know.
